Modern development relies on open-source dependencies – pre-built code components like Python packages or JavaScript libraries. These accelerate development but introduce a hidden threat: security vulnerabilities in outdated versions.
Manually tracking updates and their security implications is a daunting task.
Bito’s AI Code Review Agent automates this process, integrating seamlessly with your workflow. It analyzes code within pull requests, scrutinizing not only the code itself but also the versions of all included dependencies.
When the Agent finds a vulnerable dependency, it adds a “Security Concerns” report directly to your pull request review.
This report details the exact package, the vulnerable version you’re using, and the security threats involved. But the Agent doesn’t stop there – it recommends secure alternative versions and pinpoints the exact lines of code to change, making updates a breeze.
Example
I ran the AI Code Review Agent on one of my pull requests, and it identified some security concerns.
Let’s take a closer look at the report:
The Problem
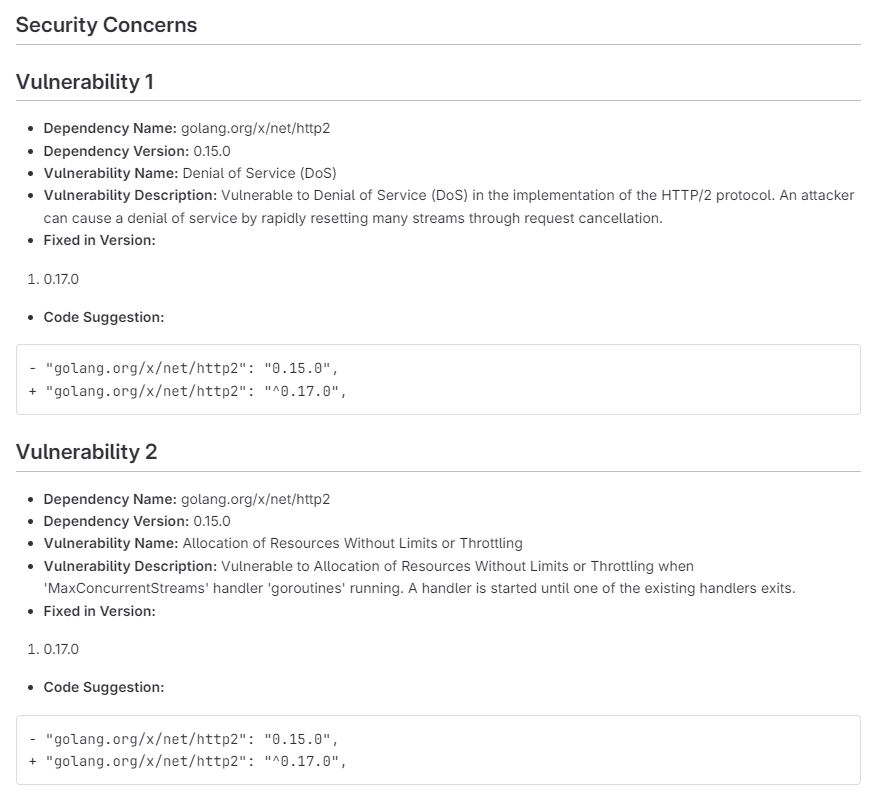
The Agent flagged two vulnerabilities in the golang.org/x/net/http2 dependency, currently at version 0.15.0. These vulnerabilities could potentially allow attackers to disrupt the application’s functionality.
Vulnerability 1: Denial of Service (DoS)
An attacker could exploit this vulnerability to crash the application by rapidly resetting connections (streams) in the HTTP/2 protocol. This would prevent legitimate users from accessing the application.
Vulnerability 2: Uncontrolled Resource Allocation
This vulnerability allows an attacker to potentially overwhelm the application with requests, causing it to run out of resources and crash. This could happen by exploiting the lack of limits or throttling on the number of concurrent streams and handler routines.
The Solution
The report recommends updating the dependency to version 0.17.0 (or later, denoted by “^0.17.0”). This fixed version addresses both vulnerabilities and helps keep the application secure.
How to use the AI Code Review Agent?
The AI Code Review Agent integrates seamlessly with your GitHub or GitLab repositories, offering both manual and automatic code review options. This flexibility allows you to leverage the Agent’s expertise whenever you need it.
Follow this simple guide to integrate the Agent with your repository.
Once set up, the Agent automatically scans new pull requests for outdated dependencies with known security vulnerabilities. If Bito finds any, it adds a “Security Concerns” report directly to the code review. If there are no outdated dependencies with vulnerabilities, then the Agent skips this report altogether.
Alternatively, for on-demand checks, simply type /review in a pull request comment and submit it.
Conclusion
By integrating seamlessly with your workflow, the AI Code Review Agent goes beyond simply identifying outdated dependencies. It fosters a security-conscious environment by highlighting potential vulnerabilities within pull requests. This sparks discussions about security best practices, ensuring everyone on your team is aware of potential risks.
But Bito doesn’t stop there. Its proactive approach identifies and addresses vulnerabilities before they can be exploited. This minimizes the risk of security breaches and safeguards your application from evolving threats. By leveraging the AI Code Review Agent, you can ensure a secure and future-proof development process, allowing you to deliver reliable and trustworthy software with confidence.