Writing secure code is critical in today’s digital landscape. Even minor vulnerabilities can be exploited by malicious actors, leading to data breaches and other security incidents. AI Code Review Agent can be a valuable tool in your arsenal to help identify and fix these vulnerabilities before they become a problem.
In this blog post, we’ll explore how AI Code Review Agent can help you write more secure code. We’ll look at two specific examples of security issues detected by the Agent and discuss the recommended solutions to address these issues.
The Agent’s specialized /review security command performs an in-depth analysis of your code to identify vulnerabilities that could allow attackers to steal data, gain unauthorized access, or disrupt your application. This includes checking for weaknesses in input validation, output encoding, authentication, authorization, and session management. It also looks for proper encryption of sensitive data, secure coding practices, and potential misconfigurations that could expose your system.
Example # 1
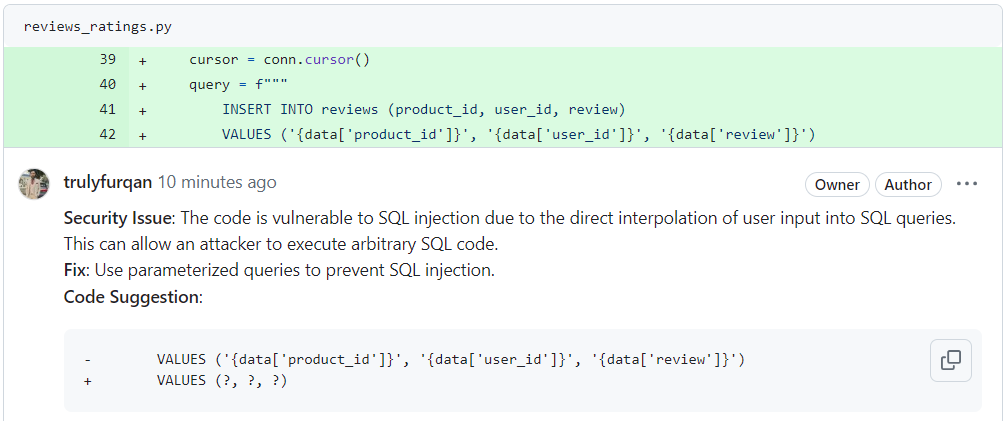
The Problem
The AI Code Review Agent identified a significant security flaw related to SQL injection in this code. The code directly integrates user input into SQL queries without proper validation. This practice makes the application vulnerable to SQL injection attacks, where an attacker could manipulate the input to execute arbitrary SQL commands, potentially gaining unauthorized access to the database.
The Solution
To address this issue, the Agent suggested using parameterized queries instead of direct string interpolation. This approach treats user inputs as data, not executable code, which effectively prevents SQL injection attacks.
Example # 2
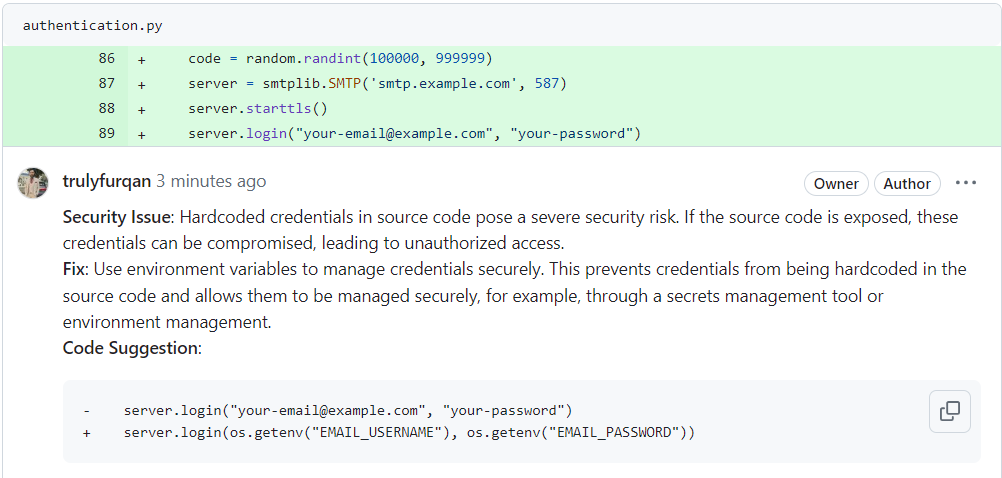
The Problem
The AI Code Review Agent discovered hardcoded credentials in the source code. Storing sensitive information such as usernames and passwords directly in the code is highly risky. If the source code gets exposed, these credentials can be easily compromised, leading to unauthorized access to critical services or systems.
The Solution
The Agent suggested using environment variables to store sensitive information securely. This method keeps credentials out of the source code, reducing the risk of exposure. Developers can retrieve these credentials at runtime from a secure environment, ensuring better security practices.
Using environment variables, developers can manage credentials more securely, protecting their applications from potential breaches.
How to use the AI Code Review Agent?
The AI Code Review Agent integrates seamlessly with your GitHub or GitLab repositories.
Follow this simple guide to integrate the Agent with your repository.
After that, trigger an AI Code Review Agent analysis by entering the command /review security in a comment box below the pull request. Submit the comment, and the agent will analyze the code for security issues, providing valuable feedback directly within the pull request.
Conclusion
The AI Code Review Agent’s in-depth analysis of pull requests helps timely identify security issues that could allow attackers to steal data, gain unauthorized access, or disrupt your application. It thoroughly checks for weaknesses in the code, ensuring proper encryption of sensitive data, adherence to secure coding practices, and identification of potential misconfigurations that could expose your system.
By leveraging the AI Code Review Agent, you can streamline the process of securing your code and better protect your application and users from security threats.